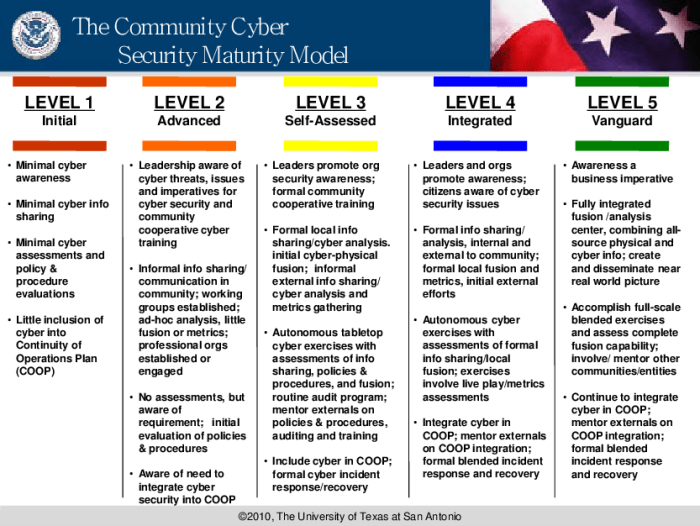
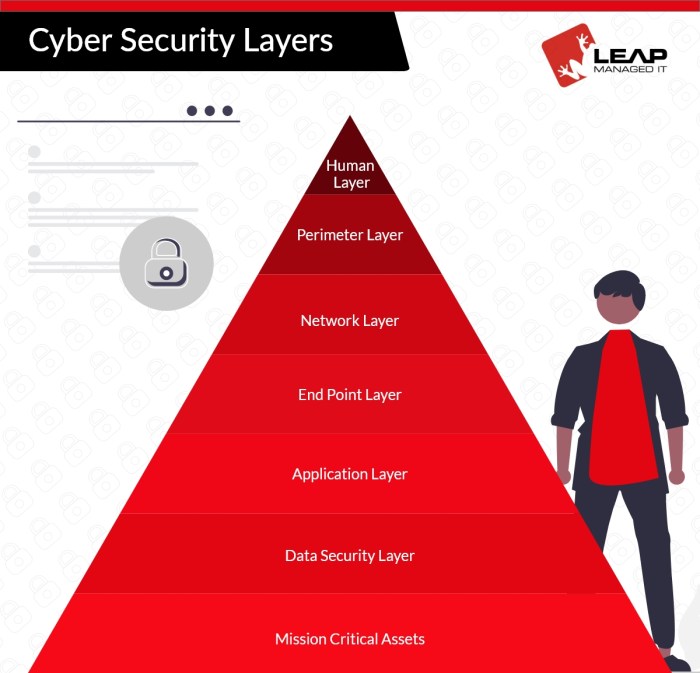
CPCon establishes a protection priority focus on critical, recognizing the paramount importance of safeguarding critical systems and data against evolving cyber threats. This comprehensive approach ensures the resilience and integrity of infrastructure essential to national security, economic stability, and public well-being.
CPCon’s mission is to identify, assess, and prioritize critical infrastructure protection needs, leveraging collaboration and information sharing among stakeholders to enhance collective defense capabilities.
1. Protection Priority Focus on Critical

In cybersecurity, “critical” refers to systems, data, or assets that are essential for the functioning of a society or organization. These systems and data are highly vulnerable to cyberattacks and can have devastating consequences if compromised.
Prioritizing the protection of critical systems and data is crucial to ensure the resilience of critical infrastructure and protect against potential threats. Critical systems include those that provide essential services such as energy, water, transportation, and healthcare. Critical data includes sensitive information such as financial records, personal data, and intellectual property.
CPCon’s Role in Establishing Protection Priorities, Cpcon establishes a protection priority focus on critical
CPCon (Cyber Protection Center) is responsible for protecting critical infrastructure in a specific region or country. Its mission is to identify, assess, and prioritize the protection of critical systems and data.
CPCon uses a risk-based approach to identify and assess critical systems and data. This approach involves analyzing the potential impact of a cyberattack on a system or data and the likelihood of such an attack occurring. Based on this assessment, CPCon establishes protection priorities to ensure that the most critical systems and data receive the highest level of protection.
Methods for Protecting Critical Systems
There are various methods and technologies used to protect critical systems, including:
- Access Control:Restricting access to critical systems and data to authorized users only.
- Firewalls:Blocking unauthorized access to networks and systems.
- Intrusion Detection and Prevention Systems (IDS/IPS):Detecting and preventing unauthorized access to systems.
- Data Encryption:Protecting data from unauthorized access or modification.
- Security Information and Event Management (SIEM):Monitoring and analyzing security events to identify potential threats.
The effectiveness of these methods depends on the specific context and requirements of the organization or system being protected.
Collaboration and Information Sharing
Collaboration and information sharing among stakeholders are essential for effective critical infrastructure protection. CPCon plays a vital role in facilitating collaboration and information sharing by:
- Establishing partnerships with government agencies, industry organizations, and international bodies.
- Providing a platform for stakeholders to share information on threats, vulnerabilities, and best practices.
- Coordinating response efforts to cyber incidents that affect critical infrastructure.
Collaboration and information sharing enable stakeholders to collectively address emerging threats and enhance the overall resilience of critical infrastructure.
Emerging Threats and Challenges
Critical infrastructure protection is constantly challenged by emerging threats and challenges, including:
- Ransomware:Malware that encrypts data and demands a ransom payment to decrypt it.
- Supply Chain Attacks:Targeting software or hardware suppliers to gain access to critical systems.
- Nation-State Cyberattacks:Cyberattacks carried out by governments to disrupt or sabotage critical infrastructure.
- Advanced Persistent Threats (APTs):Sophisticated and persistent cyberattacks that target specific organizations or systems.
CPCon continuously monitors emerging threats and adapts its protection priorities to address these challenges.
FAQs: Cpcon Establishes A Protection Priority Focus On Critical
What is the role of CPCon in critical infrastructure protection?
CPCon is responsible for identifying, assessing, and prioritizing critical infrastructure protection needs, facilitating collaboration and information sharing among stakeholders.
What are the methods used to protect critical systems?
Common methods include access controls, encryption, intrusion detection systems, and security monitoring.
Why is collaboration and information sharing important in critical infrastructure protection?
Collaboration and information sharing enable stakeholders to share best practices, identify emerging threats, and coordinate response efforts.